A couple of months in the past, I wrote a couple of rumor that TheFloW‘s yet-to-be-disclosed PS4/PS5 Kernel exploit was counting on an 18 yr outdated vulnerability. What appeared like an apparent troll initially, then seemed increasingly like an precise crash, has turned out to be the true deal. TheFloW has confirmed a couple of hours in the past that the Kernel exploit does certainly depend on a 2006 CVE. He has linked to a HackerOne report that accommodates particulars on the vulnerability (disclosure), however not on full exploitation.
TL,DR: for those who’re on PS4 11.00 or under, and/or on PS5 8.20 or under, you’ll need to keep put, a kernel exploit is almost definitely coming.
PS4 11.00 / PS5 8.20 Kernel exploit incoming
Hacker TheFloW has simply confirmed that he leveraged a important vulnerability from 2006 (CVE-2006-4304) with a purpose to acquire kernel entry to each the PS4 and PS5. He will current the exploit on the TyphoonCon safety convention, in a couple of weeks. But he’s already given some particulars of the vulnerability in a prolonged report on Sony’s bug bounty program on HackerOne.

TheFloW has been an insane supply of exploits and vulnerability disclosures for PlayStation gadgets, courting again to his early days on the PSP (when he was often called Total_Noob). Back then, the scene as a complete, Total_Noob included, was a bit reckless, and hack releases felt a bit extra easy. Nowadays, a variety of hackers hold issues below wraps, and the uncommon ones like TheFloW who do launch their work, undergo a extra “accountable” route, leveraging Sony’s bug bounty program.
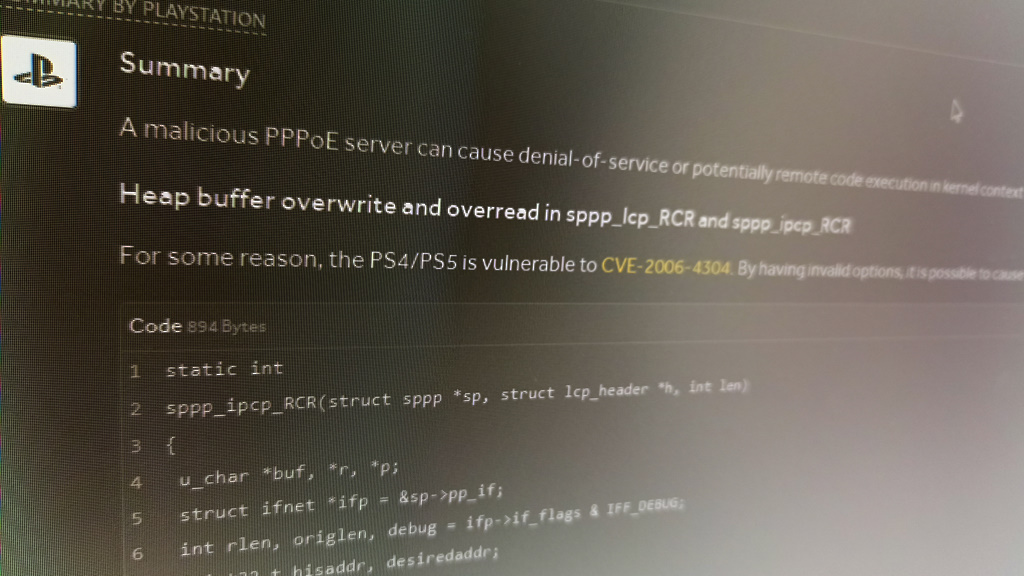
What the CVE is about:
Buffer overflow within the sppp driver in FreeBSD 4.11 by means of 6.1, NetBSD 2.0 by means of 4.0 beta earlier than 20060823, and OpenBSD 3.8 and three.9 earlier than 20060902 permits distant attackers to trigger a denial of service (panic), acquire delicate data, and presumably execute arbitrary code by way of crafted Link Control Protocol (LCP) packets with an choice size that exceeds the general size, which triggers the overflow in (1) pppoe and (2) ippp.
From TheFloW’s report:
A malicious PPPoE server may cause denial-of-service or probably distant code execution in kernel context on the PS4/PS5.

At [1], it’s potential to set len to a size between 0 and 5. Thus, at [2] len – 6 can have a unfavorable size between -6 and -1. As such, the checks for name_len and passwd_len will be bypassed, and it’s potential to have lengths as much as 255 bytes. As a consequence, at [3] it’s potential to learn out-of-bounds from the mbuf when evaluating the title and password with memcmp(). Since completely different responses are returned again based mostly on the comparability, an attacker may have the ability to use this as a an oracle to leak the out-of-bounds information (by setting the title and secret beforehand). This might be used to leak pointers and defeat KASLR remotely.
PS4 11.00 and PS5 8.20 Jailbreak – ETA WEN?
Long story quick, we’re typically getting the exploits in the end, however not earlier than PlayStation have had a while to look into them and patch them on their consoles. Hence, we already know the exploits have been patched in PS4 11.02 and PS5 8.40.
The proven fact that we’re getting this disclosure doesn’t imply a Jailbreak is correct across the nook. In current historical past, the hacker has not accomplished a full launch himself for his exploits, however as a substitute has given the scene sufficient particulars to create a working Jailbreak, which might typically take months. I’d count on issues to be comparable this time. In this case, the small print on the hackerOne bounty appear to be sufficient to set off a denial-of-service (aka a crash or kernel panic), however don’t give the precise on easy methods to craft the assault in a technique to really do greater than a crash. With that being mentioned, there are many particulars in there already (and specific “this half may leak information” sections), so I’d count on different hackers to actively be wanting into TheFloW’s report already.
Since the scene has mainly recognized about this exploit collectively for a couple of months now, some Proof of Concept code has been circulating already (instance right here from D-Link turtle). How simply these examples will be tailored based mostly on new data from the report, is one thing we nonetheless need to see.

TheFloW has said he’ll show profitable exploitation throughout his presentation at TyphoonCon in May, however not whether or not he’ll give extra technical particulars on the precise exploitation.
In different phrases, for those who’re on PS4 11.00 (or under) and/or on PS5 8.20 (or under), keep put. Now we play the ready sport, and hope that both TheFloW discloses extra data, or that different hackers determine it out based mostly on what he’s revealed already.
Source: TheFloW
Note: as at all times with such a article, I’ve accomplished my finest to be as correct as potential, however data on the subject is complicated and evolves very quickly. If you notice a mistake or inaccuracy, let me know within the feedback under. Thanks!