In context: Dynamic voltage and frequency scaling (DVFS) is a way adopted by trendy CPUs and graphics chips to handle energy and pace, adjusting frequency and voltage “on the fly” to scale back power consumption and warmth era. With a “Hot Pixels” assault, DVFS turns into yet one more channel a (very) resourceful attacker might exploit to steal knowledge and compromise person’s privateness.
Hot Pixels is a brand new side-channel assault conceived by a global group of researchersposing a theoretical safety risk that exploits Dynamic Voltage and Frequency Scaling (DVFS) strategies to “probe analog properties” of computing gadgets. DVFS is important in sustaining a fragile stability between energy consumption, warmth dissipation, and execution pace (i.e., frequency), the researchers clarify of their paper. However, it additionally introduces software-visible hybrid side-channels by way of which delicate knowledge might be extracted.
The researchers focused Arm-based SoC models, Intel CPUs, and discrete GPUs manufactured by AMD and Nvidia, as these are essentially the most prevalent microchips at the moment accessible available in the market. A side-channel assault is an assault that leverages residual data, which might be extracted as a result of inherent operational nature of a pc part, moderately than by exploiting particular safety flaws within the design.
The group examined the vulnerability of the aforementioned computing gadgets to data leakage by way of energy, temperature, and frequency values, which might be conveniently learn on a neighborhood system because of the interior sensors embedded within the chips themselves. No admin entry is critical on this case: the information is persistently accessible, and DVFS values might be manipulated to function as constants to help in figuring out particular directions and operations.
In their experiments with DVFS readings, the researchers found that passively-cooled processors (like Arm chips utilized in smartphones) can leak data by way of energy and frequency readings. Conversely, actively-cooled processors, corresponding to desktop CPUs and GPUs, can leak data by way of temperature and energy readings.
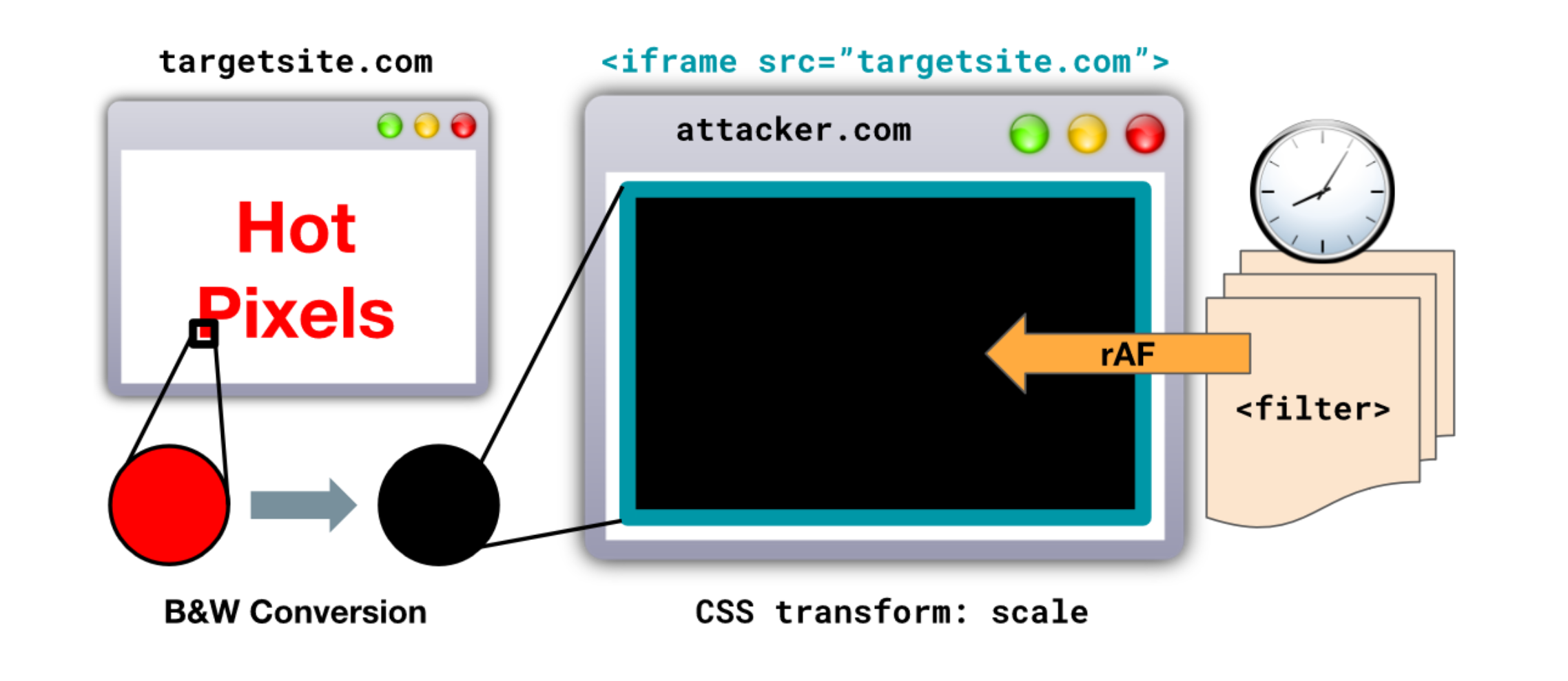
The “Hot Pixels” assaults have been thus designed as a sensible demonstration of the DVFS-related situation. This features a JavaScript-based pixel stealing proof-of-concept approach, history-sniffing assaults, and web site fingerprinting assaults. The researchers focused the most recent variations of Chrome and Safari internet browsers, with all side-channel protections enabled and normal “person” entry privileges.
The assaults might discern the colour of the pixels displayed on the goal’s display screen by way of CPU frequency leakage. They obtain this by using Scalable Vector Graphics (SVG) filters to induce data-dependent execution on the goal CPU or GPU, then utilizing JavaScript to measure the computation time and frequency to deduce the pixel shade.
The accuracy of those measurements ranges between 60% and 94%, whereas the time required to establish every pixel varies between 8.1 and 22.4 seconds. The AMD Radeon RX 6600 GPU seems to be essentially the most weak gadget to “Hot Pixels” assaults, whereas Apple SoCs (M1, M2) appear to be essentially the most safe.
In Safari, which restricts cookie transmission on iframe parts that do not share the identical origin because the dad or mum web page, researchers needed to make use of extra inventive methods. Apple’s browser is vulnerable to a sub-type of the “Hot Pixels” assault, which might infringe on the person’s privateness by extracting shopping historical past. In this case, the SVG filtering approach is used to detect the differing shade of a beforehand visited URL, reaching the next degree of accuracy starting from 88.8% (MacBook Air M1) to 99.3% (iPhone 13).
The researchers have already reported the “Hot Pixels” situation to Intel, AMD, Nvidia, and different affected corporations. However, an efficient countermeasure towards this new and complicated kind of side-channel assaults doesn’t exist but. Users needn’t be overly involved in the meanwhile, as the present pace restrict for knowledge exfiltration is a mere 0.1 bits per second, despite the fact that this could possibly be “optimized” with additional analysis.
