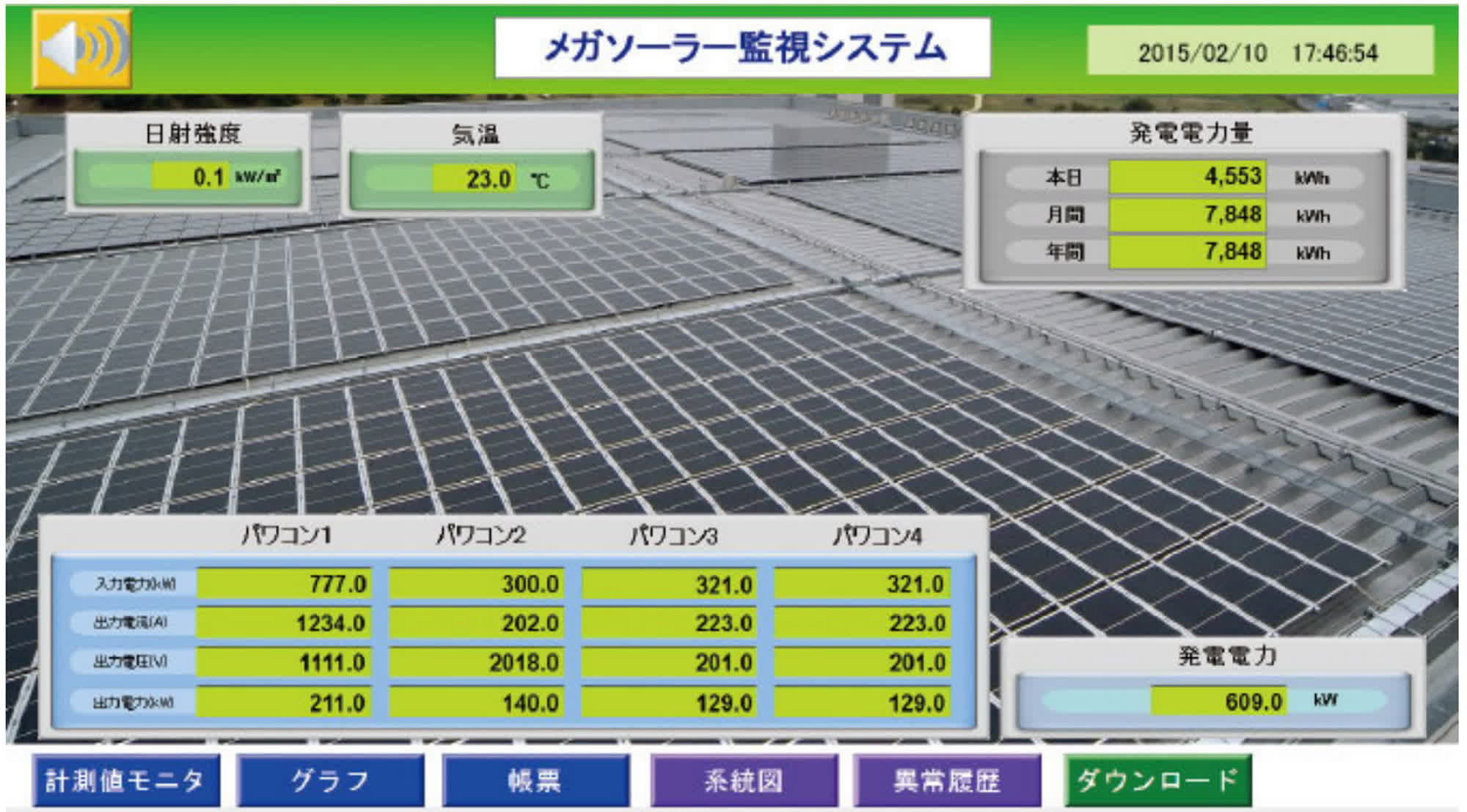
Facepalm: Contec is an Osaka-based firm that sells a devoted monitoring system for solar energy crops generally known as SolarView. Despite its widespread set up in over 30,000 energy stations, the model is affected by vital safety vulnerabilities that may be exploited remotely by attackers.
Contec explains that SolarView units are designed to “monitor and visualize” energy technology, tools standing, and error alarms in numerous kinds of solar-based energy stations. However, these monitoring units have lately raised considerations because of the presence of extreme safety vulnerabilities of their firmware, which have already been exploited.
According to “vulnerability intelligence” firm VulnCheck, the search engine for weak units, Shodan, presently indexes over 600 SolarView methods. These units are accessible by way of the open Internet, and that is a significant concern. The second challenge, tracked as CVE-2022-29303, is a command injection vulnerability with a “important” severity rating of 9.8 out of 10.
Version 6.00 of the SolarView Compact system is prone to a important safety flaw that allows distant execution of malicious instructions. Cyber-criminals have actively exploited this vulnerability to unfold a variant of the Mirai botnet, infecting routers and IoT units. If a SolarView system is compromised, it has the potential to disrupt the visibility of solar energy crops for corporations, presenting both a difficult or extremely harmful scenario relying on the applying and placement of the monitoring units.
Furthermore, VulnCheck emphasizes that the CVE description for the affected firmware model could not precisely mirror the true variety of weak units. Version 6.00 was launched in 2019, however the command injection bug continues to be current in subsequent firmware releases at the least till model 8.10 (from this 12 months).
According to VulnCheck analysts, lower than a 3rd of Internet-facing SolarView methods have been patched in opposition to CVE-2022-29303. Furthermore, there are indications that this vulnerability could have been exploited within the wild for a big interval.
Moreover, the SolarView firmware seems to be affected by extra vulnerabilities together with CVE-2023-23333, which is one other distant code execution-type flaw, and CVE-2022-44354, which may very well be exploited to add a malicious PHP webshell to a weak system.
VulnCheck emphasizes the significance for sysadmins to constantly set up the newest updates for important methods. Multiple exploits focusing on the SolarView CVE-2023-23333 flaw can be found on GitHub, and affected organizations ought to undoubtedly test the methods that seem of their public IP house and “monitor public exploits for methods that they depend on.”

